Estimated reading time: a coffee break - approx. 8 minutes
2025-10-07
Caution When Using Public Analysis Portals
I recently attended an event on cybersecurity. The presentation was overall excellent and provided valuable recommendations for the target audience. However, one point seemed problematic to me: the recommendation to upload links to virustotal.com to check whether they are phishing. I would like to expand on and differentiate this aspect here.
Executive Summary
On VirusTotal, you can enter a suspicious link and immediately receive a result. It sounds convenient - but it is not necessarily suitable for all audiences.
Where Is the Problem?
- The results are difficult to interpret and require prior knowledge, as it is often unclear what the individual ratings or warnings mean.
- Attackers also monitor the same analysis portals. If an investigation becomes public there, it can alert them early and lead to an adjustment of their tactics.
- Some links contain email addresses - visible or encoded. Encoded variants are often not recognized as personal data and may be unintentionally exposed when uploaded.
- Particularly critical are password reset links: if such tokens are uploaded, attackers could potentially take over foreign accounts.
What Does This Mean for Organizations?
- Use of such tools should be restricted to trained security personnel only.
- Employees should forward suspicious emails or links directly to the internal IT or security team.
- Organizations should define in advance which portals may be used, who may use them, and what data is permitted for upload.
In short: Checking suspicious links is important - but the responsibility belongs in professional hands.
Value for Users Without an IT Background
Public analysis portals such as VirusTotal or urlscan.io are valuable tools in responding to cybersecurity incidents. However, their use also involves risks that should not be underestimated.
The results of such portals are often difficult to understand.
An Example:
Can you clearly tell whether this sample domain is classified as a phishing site?
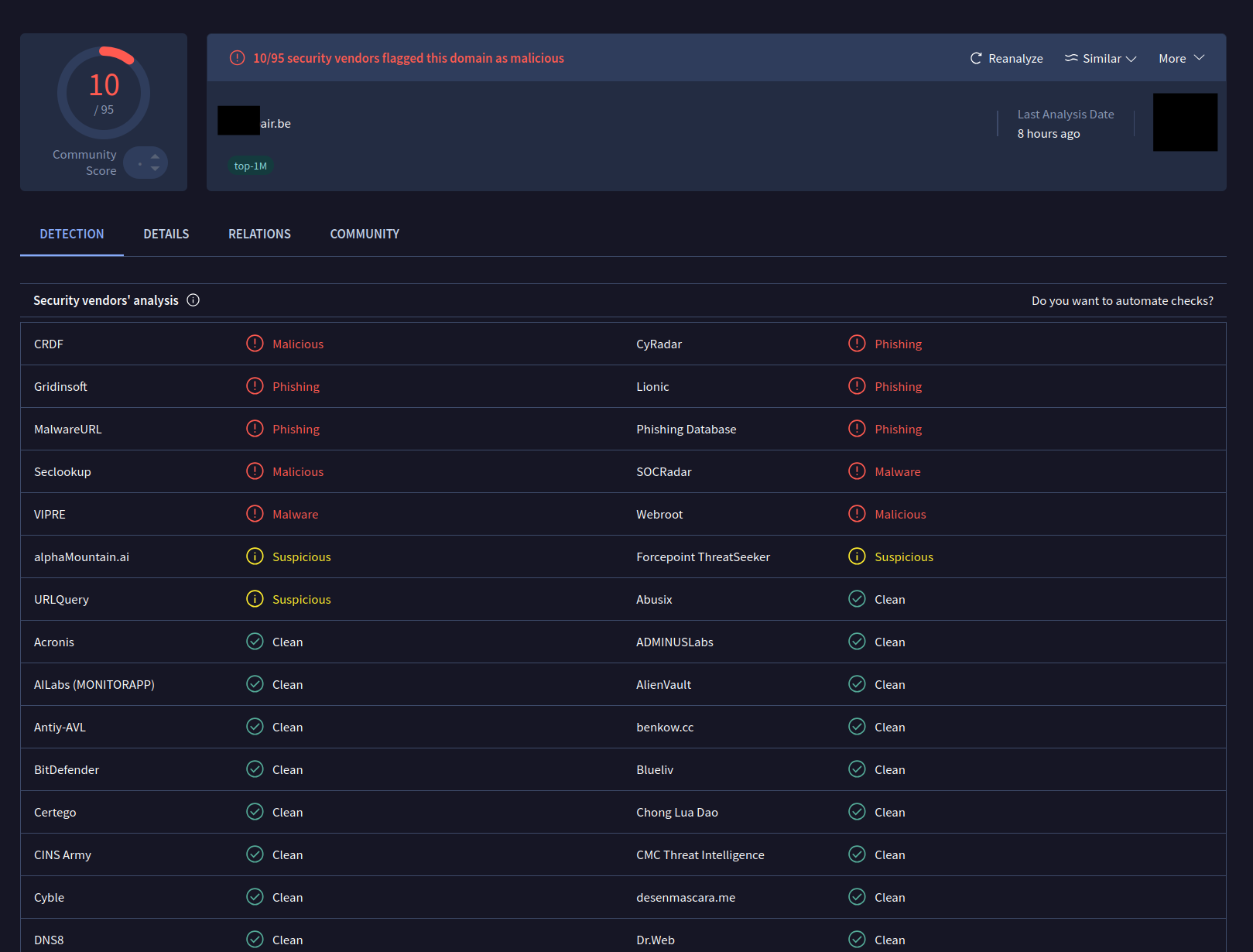
Only through additional context does it become clear that something is wrong:
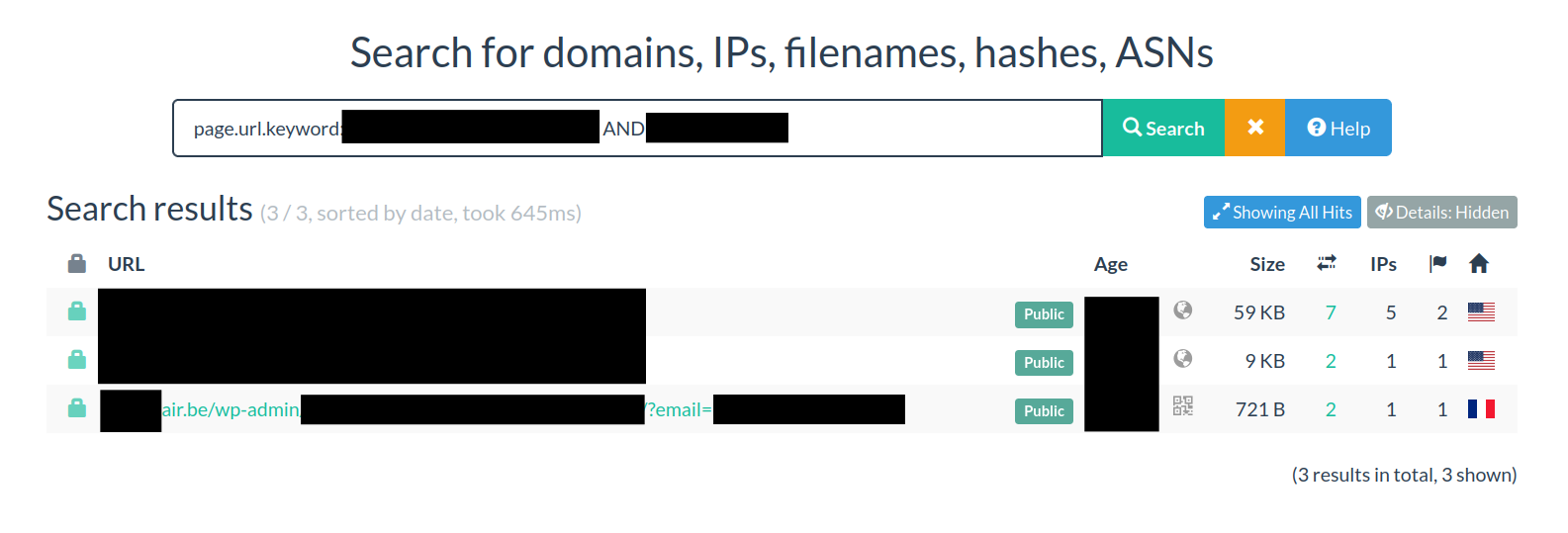
The directory /wp-admin/ indicates that a WordPress site has been compromised and that attackers have uploaded a phishing kit.
The domain itself is therefore not purely a phishing domain.
Do you think someone without cybersecurity experience would reach the right conclusion here?
Security Risks for Users of These Portals
Disclosure of Personal Data
Some links contain personal data. In the example above, the parameter ?email=… appears in the URL.
The question mark ? introduces additional information (query parameters) that a script processes - in our case, an email address.
Uploading such a link to a public portal can lead to the following risks:
- Spam: Addresses are collected and end up in spam lists.
- Targeted phishing: Criminals learn that the address is active.
- Social engineering: Combining data with company information facilitates attacks.
- Password attacks: Cross-referencing with known data leaks.
- Reputational risks: Addresses appear in threat intelligence feeds.
- GDPR concerns: Personal data may be transferred to third countries without legal basis.
Note (not legal advice):
In many cases, there is no legal basis (“Art. 6 GDPR”) for uploading personal data.
The “legitimate interest” clause does not apply, as verification can be done without an email address.
Special Cases
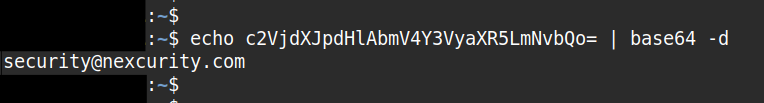
Obfuscation:
Sometimes email addresses are obfuscated, for example using Base64:?email=c2VjdXJpdHlAbmV4Y3VyaXR5LmNvbQo=
Redirects:
Some phishing kits redirect (e.g., to Wikipedia) if no email address is provided. A fake address is often enough to “pass” the test.
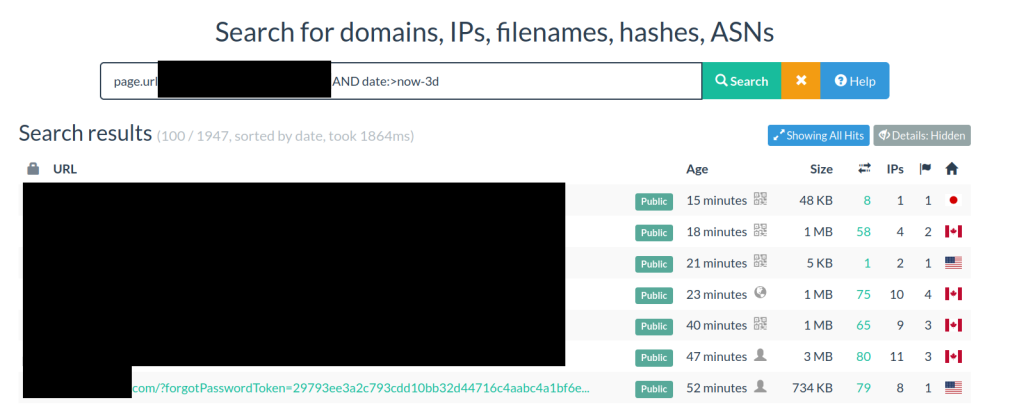
Even More Critical: Password Reset Links
It becomes especially problematic when password reset links are uploaded.
If the tokens fall into the wrong hands, accounts can be taken over.
Conclusion
Analysis platforms are valuable tools - but not for end users.
With clear processes, access control, and automation, their benefits can be used safely.
Recommendations for Action
Use of Analysis Tools:
- Raise awareness: Clearly communicate that these tools should only be used by trained personnel.
- Define procedures: Create step-by-step playbooks to ensure safe and consistent use.
- Automation: Develop internal tools (e.g., Python script or web app) for automated URL sanitization, API uploads, and result retrieval.
- Access controls: Access to analysis portals should be limited to the cybersecurity team.

Strengthening Cybersecurity:
- Technical access controls: Block URLs with suspicious paths
(/wp-admin, /wp-content). - Monitoring: Set up alerts for occurrence in log files (an indicator of email filter gaps or private account use).
Transparency notice: Some of the tools mentioned are regularly licensed or used by us. Their mention is independent. There is no cooperation, payment, or other influence from the vendors.
